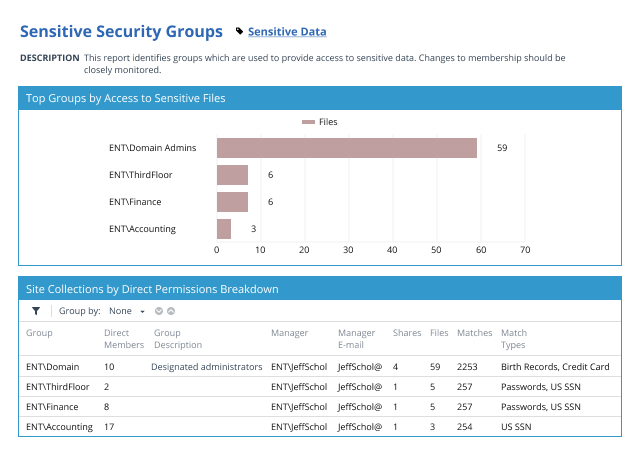
Auditing Software for File Systems
Netwrix Enterprise Auditor (formerly StealthAUDIT) for File Systems empowers you to discover, organize and secure the massive amounts of data you store in your on-premises and cloud-based file systems. Know exactly where sensitive data resides, empower data owners to enforce a least-privilege model, promptly detect and investigate suspicious user activity, and more.
Strengthen the security of your File Systems
Your on-premises and cloud-based file systems are a vital IT resource, housing huge amounts of business-critical data in documents, spreadsheets, presentations and more. Netwrix Enterprise Auditor (formerly StealthAUDIT) for File Systems empowers you to both proactively mitigate risks to that data and to promptly spot and respond to threats in progress.

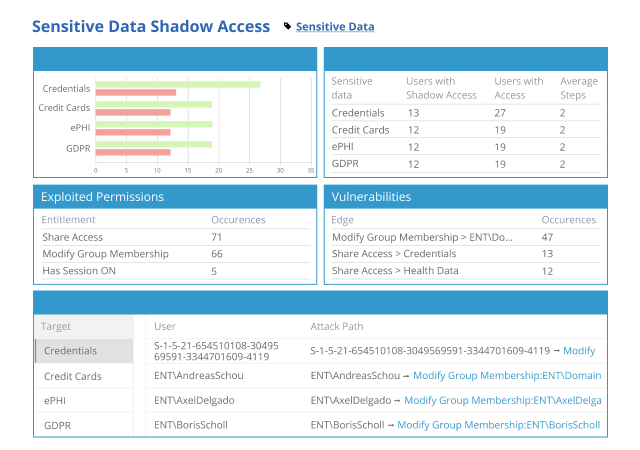
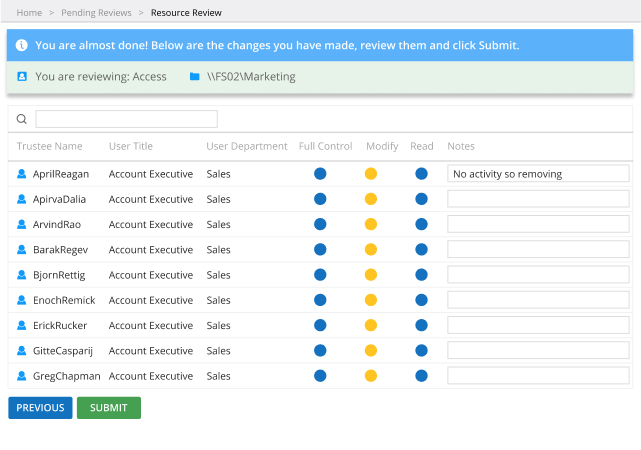
_1640080035_1669666236.jpg)