Identity and Access Management (IAM) Software Solutions
to Secure Sensitive Data
Know who has access to what, when, and why
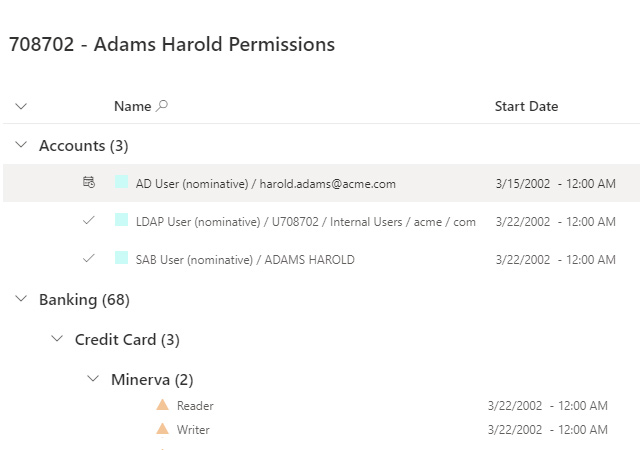
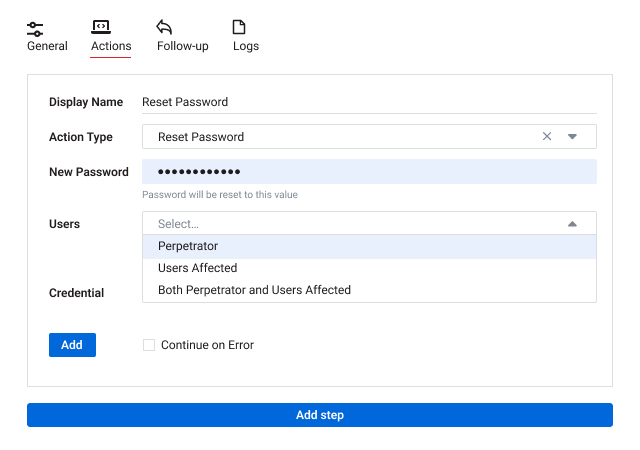
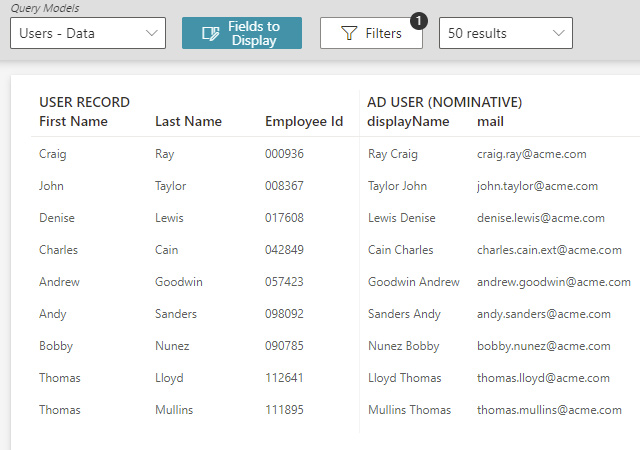
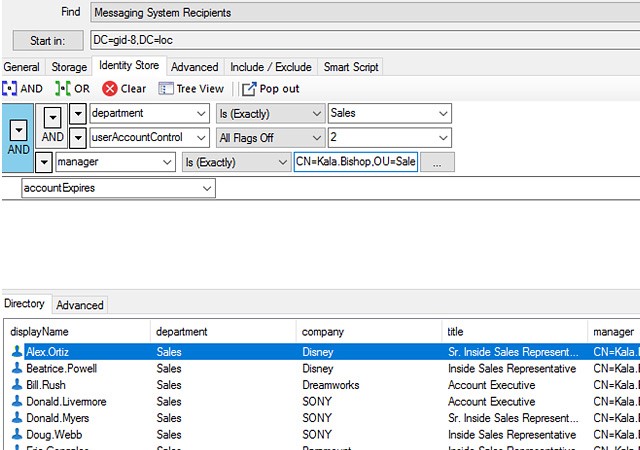
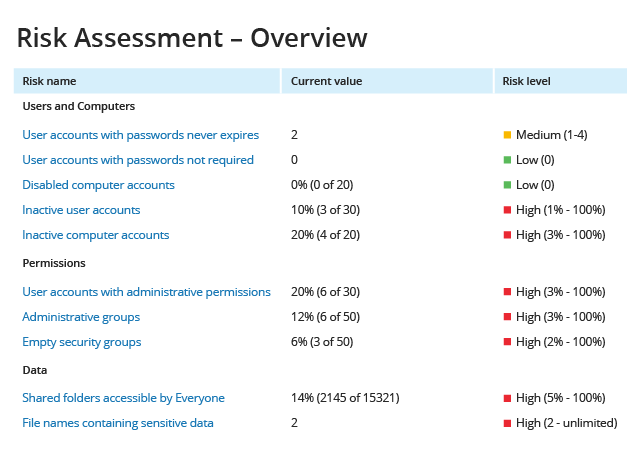
The foundation of a Zero Trust security strategy is the principle of least privilege, which requires granting each user only the access privileges they need to do their job. Accordingly, the first step in protecting your data and satisfying auditors is determining which users have access to what data, applications, and other IT resources, as well as which data is regulated or otherwise sensitive.
Minimize security risks by limiting access to sensitive data
To reduce the risk of cybersecurity incidents, organizations need to take multiple coordinated steps to manage access to all parts of the infrastructure.
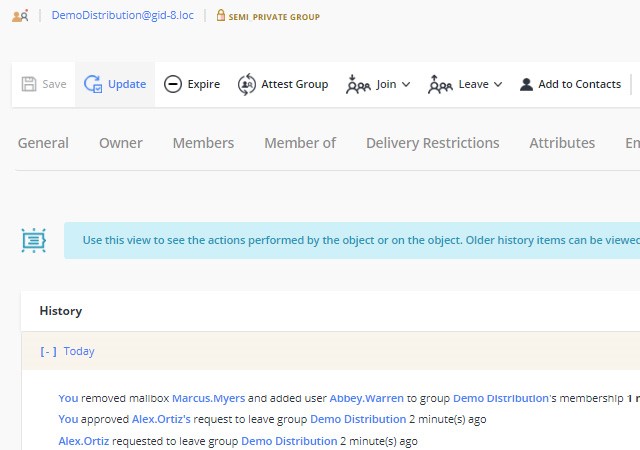
Curb the impact of identity-based incidents
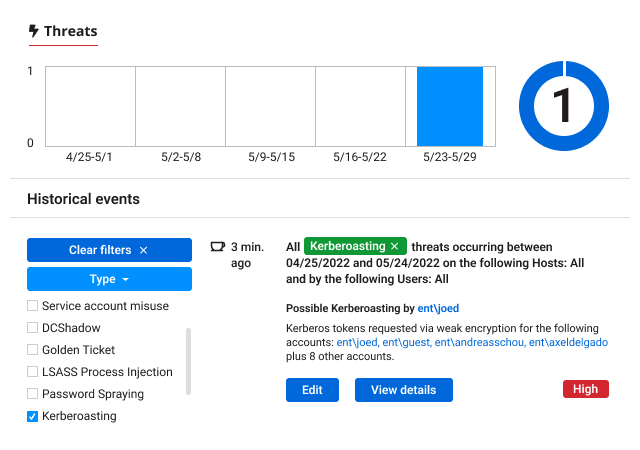
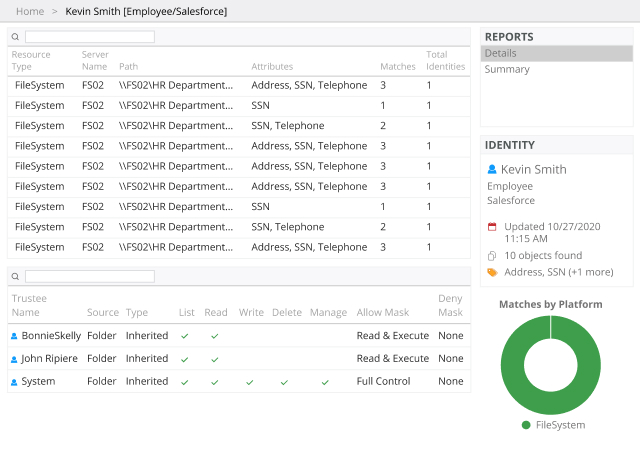
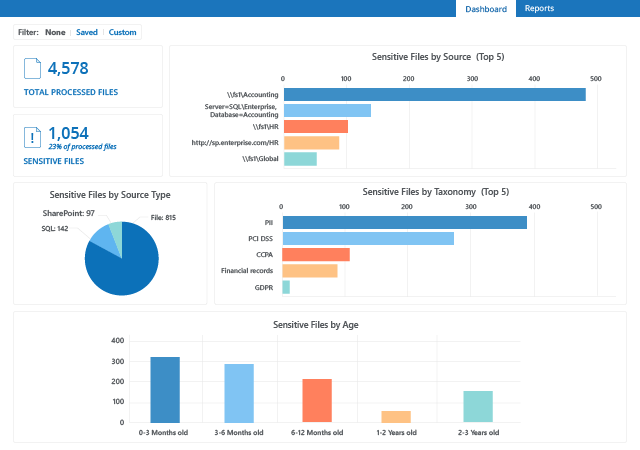
Organizations are increasingly vulnerable to identity-related breaches, with over 80% falling victim. Mitigate this risk by detecting and containing identity threats fast.
Learn more about Netwrix solutions for identity threat detection and response.
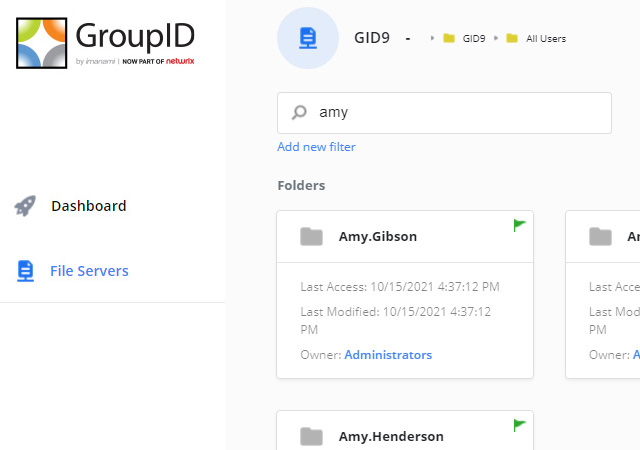
Take the stress out of your next audit
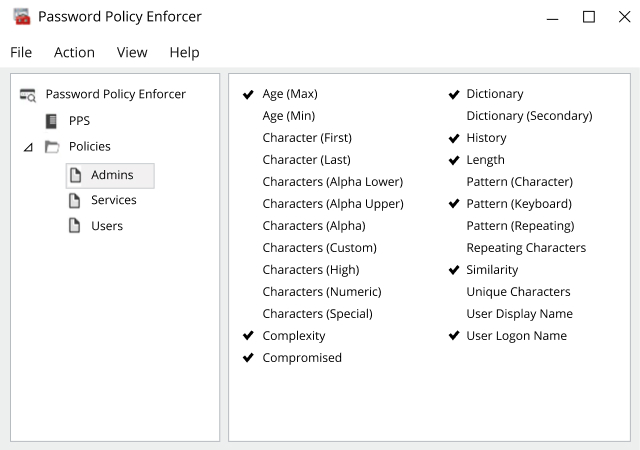
Organizations already face an alphabet soup of security and privacy regulations — PCI-DSS, GDRP, NERC, SOX, FERPA, CJIS, CMMC and so on — and more are being enacted every year. Despite their differences, they all share a key core component: strong identity and access management. Netwrix products enable you to achieve and prove compliance with these IAM requirements while reducing the impact on IT and user productivity.


.png)