Why Move from Traditional DNS to DNS over HTTPS
When your web browser accesses a website, it needs to first translate the friendly URL (such as Netwrix.com) to the public server IP address of the server that hosts that website. This is known as a DNS lookup. Traditional DNS is unencrypted, unlike modern HTTPS web traffic that’s almost entirely secured via HTTPS these days.
Since HTTPS encrypts your communications with websites once you’ve established a connection, you may be wondering why it matters that the initial DNS lookup remains unencrypted. After all, with unencrypted DNS, attackers on the same network as you can view which websites you’re browsing and potentially re-route your DNS lookups to malicious websites and phishing scams.
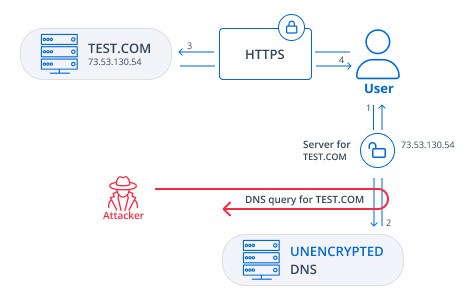
DNS over HTTPS (DoH) was introduced to prevent attackers from monitoring your browsing habits or re-directing you to malicious websites simply by snooping DNS traffic. DoH pairs DNS queries with the encryption power of HTTPS instead of communicating in plain text. Traditional DNS lookups are performed unencrypted over port 53, but DoH lookups occur inside HTTPS traffic over port 443. Starting with Windows Server 2022, the DNS client supports DNS-over-HTTPS; it can be enabled for all applicable Active Directory machines through Group Policy.
This is the simple, high-level view of DNS over HTTPS, but it’s all you really need to know from an end-user perspective. It’s a best practice to enable DNS over HTTPS when possible, which is what we’ll outline below for Windows 10.
While out of the scope of this blog, Apple has also announced DNS over HTTPS (DoH) support for iOS/macOS, and Cloudflare offers their powerful 1.1.1.1 DNS resolver to add DNS lookup security to various mobile and desktop operating systems.
Many web browsers, including Firefox and Chromium-based browsers, also support DoH if you’d prefer to enable it on a per-application basis rather than at the OS-level. However, enabling DoH in your OS benefits applications that don’t natively support DoH by giving them that ability. Plus, DNS lookups have traditionally been a function of the OS rather than web browsers.
How To Enable DNS over HTTPS in Windows 10
Enabling DNS over HTTPS in Windows 10 provides the functionality for all users and applications requesting DNS lookups, including all web browsers. Keep in mind Windows 10 should be up to date to ensure the DoH feature is available.
Enabling DoH in the Windows 10 Registry
To enable DNS over HTTPS in the Windows 10 registry (Build 19628 or higher):
- Open the Registry Editor
- Navigate to: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesDnscacheParameters
- Create a new DWORD named “EnableAutoDoh” and give it a value of 2.
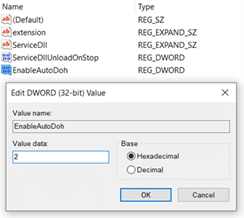
Windows 10 Registry Editor with “EnableAutoDoh” added to enable DNS over HTTPS.
- Reboot the host.
- Change your network connection’s primary and alternate DNS servers, under your adapter’s Internet Protocol Version 4 (TCP/IPv4) properties in network configuration.
The following server addresses are currently supported for DNS over HTTPS in Windows 10:
- Cloudflare — Primary: 1.1.1.1, Alternate: 1.0.0.1
- Google — Primary:8.8.8.8, Alternate: 8.8.4.4
- Quad9 — Primary: 9.9.9.9, Alternate: 149.112.112.112
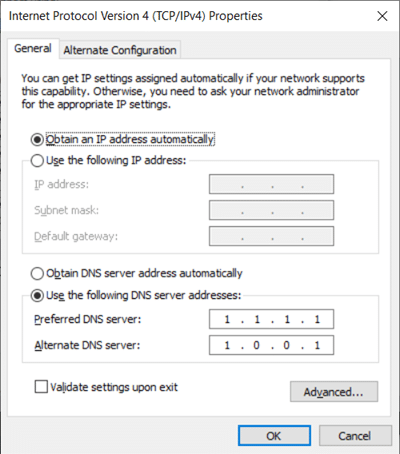
A network adapter’s “Internet Protocol Version 4 (TCP/IPv4)” properties in Windows 10, configured to use Cloudflare for DNS over HTTPS
Enabling DoH via the Windows 10 Settings > Network & Internet Menu
To enable DNS over HTTPS in the Settings > Network & Internet menu (Build 20185 or higher):
- Select Settings in the Start menu.
- Open Network settings.
- Under Network status, open the Properties menu for the desired internet connection.
- Click Edit under DNS settings.
- Select the Manualoption, and then specify the Preferred DNS and Alternate DNS IP addresses. DNS providers currently supported by Windows 10 are:
- Cloudflare – Primary: 1.1.1.1, Alternate: 1.0.0.1
- Google – Primary:8.8.8.8, Alternate: 8.8.4.4
- Quad9 – Primary: 9.9.9.9, Alternate: 149.112.112.112
- Select Encrypted only (DNS over HTTPS) for encryption under Preferred DNS and Alternate DNS.
- If desired, you can configure the same for IPv6 (the previous steps were for IPv4).
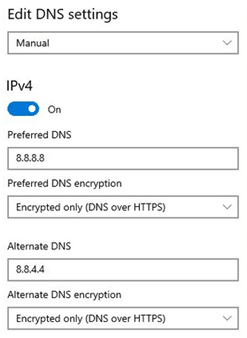
Windows 10 with DNS over HTTPS enabled
Per Microsoft, “Once encryption is enabled, you can confirm it’s working by looking at the applied DNS servers in the network properties and see them labelled as ‘(Encrypted)’ servers.”
Enabling DoH via Group Policies
Since Windows Server 2022, it is possible to enable DoH on the domain level. Changing DNS over HTTPS settings globally is possible via the Configure DNS over HTTPS (DoH) name resolution policy, which can be found in the Group Policy Editor in the Computer ConfigurationPoliciesAdministrative TemplatesNetworkDNS Client section:
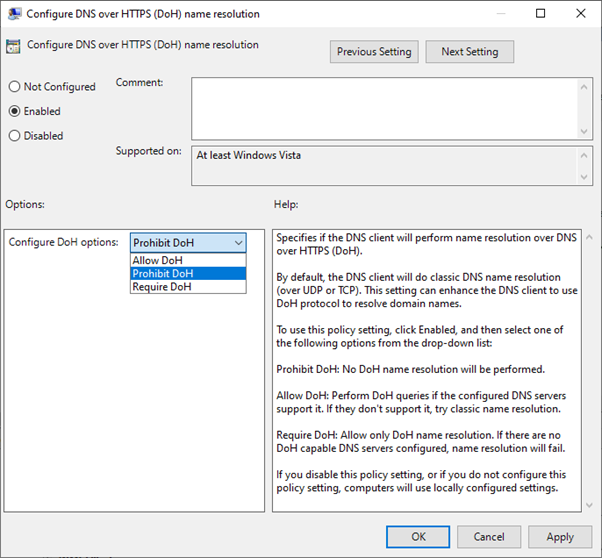
If you want to add new DoH server to the list of known servers, you can use the Add-DnsClientDohServerAddress PowerShell cmdlet.
You can check the list of DoH servers used for name resolution via PowerShell with following command: Get-DNSClientDohServerAddress.
FAQ
What is DNS over HTTPS?
DNS over HTTPS (DoH) is a protocol for performing remote Domain Name System (DNS) resolution via the HTTPS protocol.
Should I use DNS over HTTPS?
With DoH enabled, you’ll be able to bypass censorship, improve the security of your network traffic and increase your network’s privacy.
Is DNS over HTTPS enabled by default?
No, you will have to enable it manually on your workstation or via Group Policy.
How do I enable HTTPS over DNS?
To enable DNS over HTTPS in Windows 10, open the Network & Internet section in Settings, go to Status, click Properties and select Edit IP assignment or Edit DNS server assignment.
How do I check DNS over HTTPS settings?
To check your DNS over HTTPS settings, open the Network & Internet section in Settings, go to Status, click Properties and select Edit IP assignment or Edit DNS server assignment.
Does Windows 10 support DNS over HTTPS?
DoH is supported in Windows 10 builds 19628 or higher.


