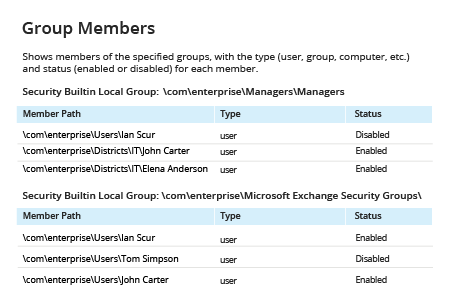
To See Which Groups a Particular User Belongs to:
- Open the command prompt by navigating to Start → Run (or pressing Win + R) and entering "cmd".
- Type the following command in the command line, specifying the user account you want to find group membership for:
net userusername
- At the end of the resulting report, you will find a list of the local groups and global groups that the user belongs to:
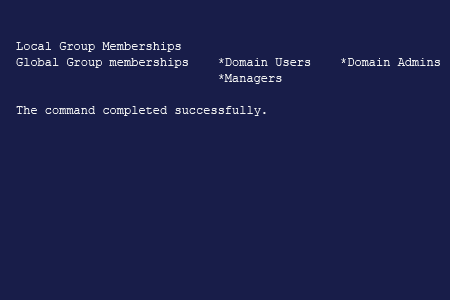
To List All the Users in a Particular Group:
- Open the command prompt by navigating to Start → Run (or pressing Win + R) and entering "cmd".
- Enter the following command, specifying the required group name:
net group groupname
- At the end of the resulting report, you will find a list of the members of the group:
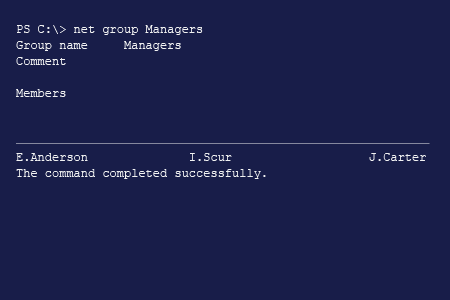
NET commands also work for Windows 10 local users and groups.
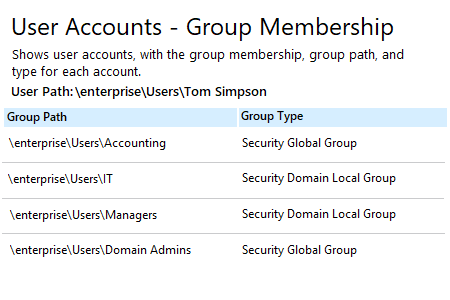
To See Which Groups a Particular User Belongs to:
- Run Netwrix Auditor → Navigate to "Reports" → Click “Predefined” → Expand the "Active Directory" section → Go to "Active Directory - State-in-Time" → Select "User Accounts - Group Membership"→ Click “View".
- Specify “Enabled” in the “Status” field and type “user” in the “Member Type” field -> Click “View Report”.
To List All the Users in a Particular Group:
- Run Netwrix Auditor → Navigate to “Reports” → Click “Predefined” → Expand the “Active Directory” section → Go to “Active Directory – State-in-Time” → Select “Group Members” → Click “View”.
- Set up the following filters:
- Status: Enabled
- Member Type: User
- Group path: The group path. You can specify the partial path to a particular group, using % as a wildcard character, or leave wildcard to see report for all groups.
- Click “View Report”.