Reduce the risk of a data breach, pass compliance audits and enhance IT productivity with Netwrix Enterprise Auditor
Tired of juggling multiple point solutions in a never-ending struggle to properly manage and secure your critical data repositories, core systems and applications, and other IT assets systems? Get the answers and control you need from a single extensible platform. Netwrix Enterprise Auditor (formerly Netwrix StealthAUDIT) automates the collection and analysis of the data you need to minimize your attack surface, prove regulatory compliance, automate threat remediation and more.
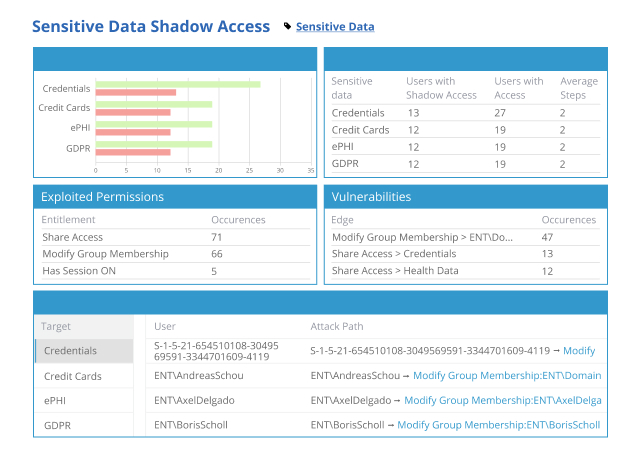
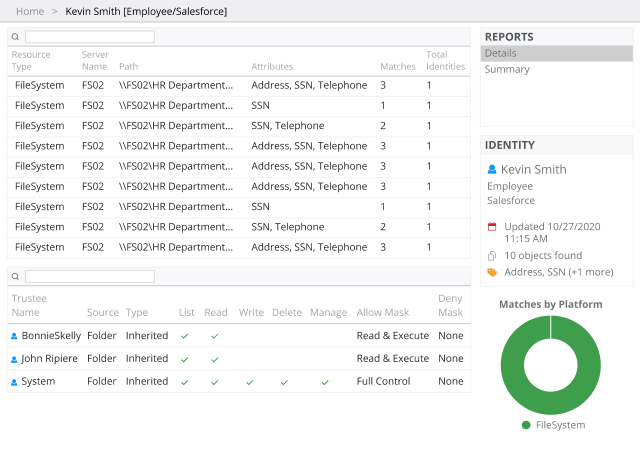
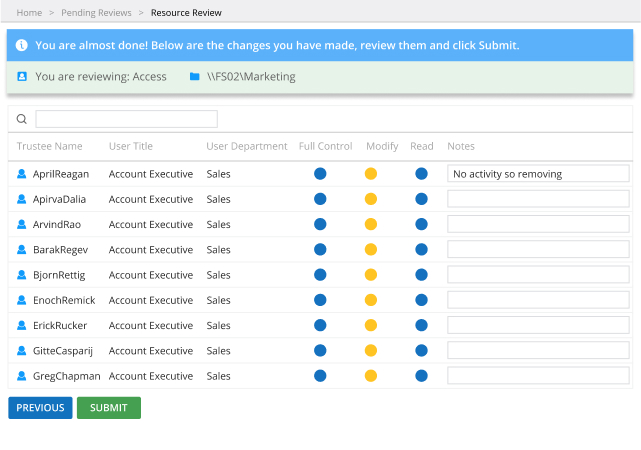
Govern access to critical data, systems and applications from one powerful solution
Secure your sensitive data wherever it resides with 40+ built-in data collection modules covering both on-premises and cloud-based platforms. A wizard-driven interface makes it easy to gather exactly the data you need, and the agentless architecture makes the data collection process fast and lightweight. Supported systems include:
Plus, use our free resource connectors to extend Netwrix Enterprise Auditor to virtually any content repository you use, including: Microsoft Hyper-V, VMware, Google Drive, SalesForce, MySQL, and more!
Stay in control of your IT assets with the Netwrix Enterprise Auditor reporting and access governance platform